Custom Logs (API)
If you want to send custom logs to the Middleware backend, you can use the provided API. This documentation covers how you can use the API to send the custom logs to the Middleware backend and how the data can be accessed via the Middleware dashboard.
Before you begin
- Endpoint:
https://demo.middleware.io/v1/logs - Auth: pass your Middleware API key in the
Authorizationheader.
Endpoint
POST https://demo.middleware.io/v1/logsAuthentication
Include your Middleware API Key in:
Authorization: <MW_API_KEY>Sample cURL
You can refer to this sample curl request to understand how to ingest custom logs to Middleware. Request Body fields are explained in the next section.
curl -X POST "https://demo.middleware.io/v1/logs" \
-H "Accept: application/json" \
-H "Content-Type: application/json" \
-H "Authorization: <MW_API_KEY>" \
-d @- << 'EOF'
{
"resource_logs": [
{
"resource": {
"attributes": [
{ "key": "mw.resource_type", "value": { "string_value": "custom" } },
{ "key": "service.name", "value": { "string_value": "nginx-123" } }
]
},
"scope_logs": [
{
"log_records": [
{
"severity_text": "WARN",
"body": { "string_value": "upstream server is not accepting request" },
"severity_number": 11,
"attributes": [
{ "key": "server", "value": { "string_value": "nginx" } }
],
"time_unix_nano": 1759750270000000000
}
]
}
]
}
]
}
EOFUnderstanding resource attributes
resource_logs → resource → attributes
| Key | Compliance Level | Description |
|---|---|---|
mw.account_key | required | Will be required to authenticate your data with your Middleware account |
mw.resource_type | required | Will be required to label the log source as "custom" |
service.name | optional | Can be helpful to filter the data in the Logs module |
Understanding log records
resource_logs → scope_logs → log_records
| Key | Compliance Level | Description |
|---|---|---|
severity_text | optional | One of FATAL, ERROR, WARN, INFO, DEBUG, TRACE |
severity_number | optional | 1-4 : TRACE, 5-8 : DEBUG, 9-12 : INFO, 13-16 : WARN, 17-20 : ERROR, 21-24 : FATAL |
body | required | The actual log body you want to ingest (string_value) |
time_unix_nano | required | Timestamp for your log in nanoseconds since epoch |
Verify delivery
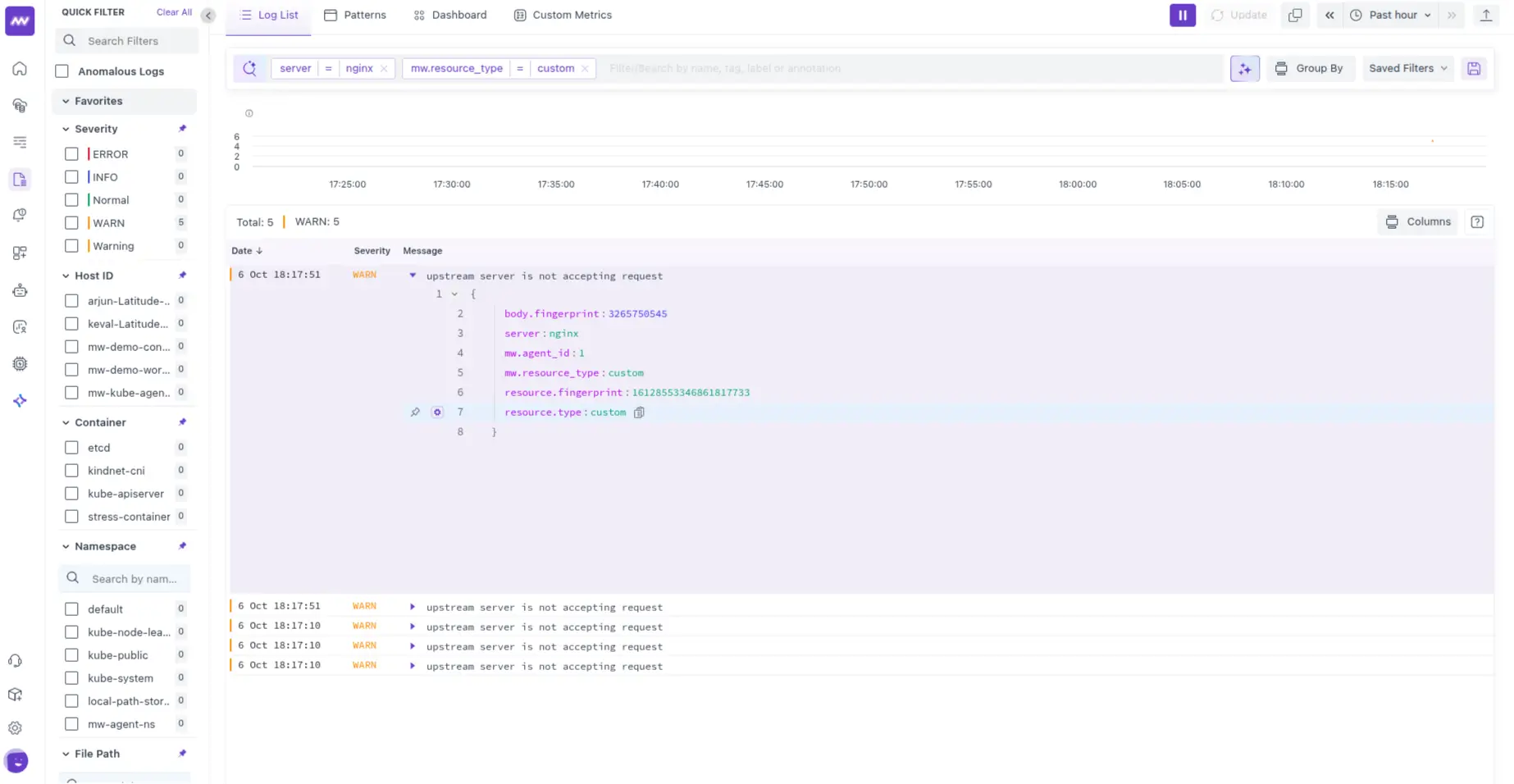
Once you send data to the Middleware backend, you can access verify the data from the logs section. It can be further filtered using the custom attributes you have used in the cURL request.
For example, in the sample cURL request, we have used mw.resource_type = custom.
Troubleshooting
- 401/403 (auth): Use header exactly
Authorization: <YOUR_MW_API_KEY>(no “Bearer”). Includemw.account_keyinresource.attributesand ensure key/account match. - 400 / schema issues: JSON must be valid. Required:
mw.account_key,mw.resource_type="custom",body.string_value,time_unix_nano(number). Keep exact casing (string_value, notstringValue). - Logs not visible:
time_unix_nanomust be nanoseconds (≈19 digits), not ms. Widen the time range and start with filtermw.resource_type=custom; refine byservice.nameif needed. - Severity looks off: Use
severity_textfrom {FATAL, ERROR, WARN, INFO, DEBUG, TRACE}. Keepseverity_numberwithin documented bands. - Batch too big / 413 / flakiness: Send smaller batches (e.g., 500–1000 log records) and add retry with exponential backoff for 429/timeouts.
- CORS/proxy/TLS hiccups: Call the endpoint from server/agent code (not browser). If behind a corporate proxy, trust its CA or bypass interception for
demo.middleware.io. - Endpoint/headers sanity check:
POST https://demo.middleware.io/v1/logswithContent-Type: application/jsonandAccept: application/json.
Need assistance or want to learn more about Middleware? Contact our support team at [email protected] or join our Slack channel.